The settings for encryption and authentication on the WLAN networks are configured under . The following encryption profiles are stored by default and these can be used for the configuration of the WLAN networks.
- P-NONE
- No encryption, the SSID is open.
- P-PSK-WPA2
- The authentication method used is WPA2 with pre-shared key (PSK), also known as WPA2-Personal. A key must be configured for the WLAN network.
- P-PSK-WPA2-3
- The authentication method used is WPA2 and/or WPA3 with pre-shared key (PSK), also known as WPA-Personal. A key must be configured for the WLAN network.
- P-PSK-WPA3
- The authentication method used is WPA3 with pre-shared key (PSK), also known as WPA3-Personal. A key must be configured for the WLAN network.
- P-PSK-WiFi7
-
Ccertain encryption settings are mandatory for standards-compliant Wi‑Fi 7 and Multi Link Operation:
- The WPA session key type must include AES-GCMP-256
- The Group Mgmt Cipher must be BIP-GMAC-256
- The SAE/OWE-DH groups must include DH-19, DH-20, and DH-21
- Protected Management Frames (IEEE 802.11w) must be enabled
- Beacon Protection must be enabled
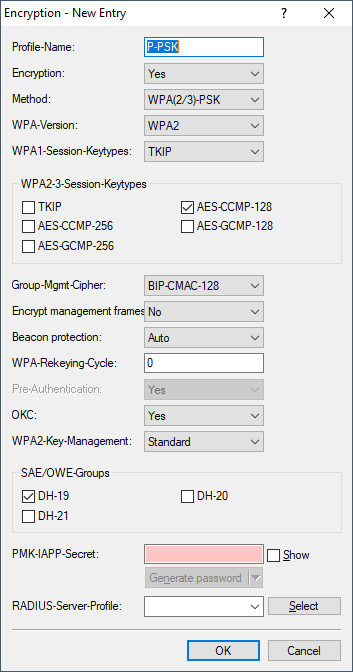
- Profile-Name
- Choose a meaningful name for the encryption profile here. This internal identifier is used to reference the encryption profile from other parts of the configuration.
- Encryption
- Here you configure whether the WLAN network should be encrypted or if no encryption should be used (Open Network).
- Method
-
Here you configure the encryption method. The following
methods are available:
- WPA
- WPA(2/3)-PSK: WPA2 and/or WPA3 with pre-shared key (PSK), also known as WPA-Personal.
-
WPA(2/3)-802.1X: WPA2 and/or WPA3 with 802.1X, also known as WPA-Enterprise
Important: Note that 802.1X requires a RADIUS server profile to be specified as well.
- WEP
-
Important: The WEP process no longer provides adequate security and should only be used to integrate legacy clients that do not support a newer security method. If this is the case, we recommend that you isolate the WEP clients in their own VLAN to keep them separate from the rest of the WLAN infrastructure.
- WEP-40-Bits: WEP with 40-bits key length
- WEP-104-Bits: WEP with 104-bits key length
- WEP-128-Bits: WEP with 128-bits key length
-
WEP-40-Bits-802.1X: WEP with 40-bits key length and 802.1X
Important: Note that 802.1X requires a RADIUS server profile to be specified as well.
-
WEP-104-Bits-802.1X: WEP with 104-bits key length and 802.1X
Important: Note that 802.1X requires a RADIUS server profile to be specified as well.
-
WEP-128-Bits-802.1X: WEP with 128-bits key length and 802.1X
Important: Note that 802.1X requires a RADIUS server profile to be specified as well.
- Enhanced-Open
-
Until now, hotspots were mainly operated without encryption, meaning that the data transmitted over the
wireless interface was open to inspection. What also offers only limited security is the widespread
practice of securing a hotspot with WPA2-PSK and publicly announcing the shared key, for example, on a
poster. Since WPA2-PSK does not offer Perfect Forward Secrecy, an attacker who knows this key can use it
to subsequently decrypt recordings of secure data traffic. The Enhanced Open method minimizes these
risks. Clients that support this method use encrypted communication to prevent other users in the same
radio cell from eavesdropping on their communications. The threat of a man-in-the-middle attack remains,
but the risk is much lower than when using an unencrypted open hotspot. Just set the encryption method.
That is all you need to do to encrypt communications for clients that support this method.
Note:
Clients, which don't support the encryption method Enhanced-Open cannot connect to the WiFi network.
- WPA-Version
-
Wi‑Fi Protected Access (WPA) is an encryption
method. Here you configure the WPA version used for the encryption methods WPA(2)-PSK and WPA(2)-802.1X. The
following versions are available:
- WPA1: WPA version 1 is used exclusively.
- WPA2: WPA version 2 is used exclusively.
- WPA3: WPA version 3 is used exclusively.
- WPA1/2: Whether the encryption method WPA 1 or 2 is used depends on the capabilities of the client.
- WPA2/3: Whether the encryption method WPA 2 or 3 is used depends on the capabilities of the client.
- WPA1-Session-Keytypes
-
Here you configure the session key type
to be used for WPA version 1. This also influences the encryption method used. The following types are
available:
- TKIP
- TKIP encryption is used.
- AES
- AES encryption is used.
- TKIP/AES
- Whether the encryption method TKIP or AES is used depends on the capabilities of the client.
Note: Employing TKIP is only recommended for operating older WLAN clients which do not support AES.Note: If a WLAN network uses only WEP or WPA with TKIP for encryption, the WLAN clients connected to it achieve a maximum gross data rate of 54 Mbps. - WPA2/3-Session-Keytypes
-
Configure here which session key type should be offered for WPA version 2 or 3. This also influences the encryption
method used. The following types are available for selection:
- TKIP
- TKIP encryption is offered.
- AES-CCMP-128
- This procedure of the Advanced Encryption Standard (AES) is offered.
- AES-CCMP-256
- This procedure of the Advanced Encryption Standard (AES) is offered.
- AES-GCMP-128
- This procedure of the Advanced Encryption Standard (AES) is offered.
- AES-GCMP-256
- This procedure of the Advanced Encryption Standard (AES) is offered.
Note: For maximum compatibility with legacy clients, the sole setting AES-CCMP-128 should be used. Please note that IEEE 802.11be standard-compliant operation requires the use of AES-GCMP-256. Based on experience, current Wi‑Fi 7 clients also support other encryption methods, such as AES-CCMP-128, or combinations thereof. This is especially important when operating mixed SSIDs for Wi‑Fi 7 and older clients, which generally only support AES-CCMP-128. If in doubt, use a separate SSID for Wi‑Fi 7 with the appropriate encryption settings.Note: Employing TKIP is only recommended for operating older WLAN clients which do not support AES.Note: If a WLAN network uses only WEP or WPA with TKIP for encryption, the WLAN clients connected to it achieve a maximum gross data rate of 54 Mbps. - Encrypt management frames
-
By default, the management
information transmitted on a WLAN for establishing and operating data connections is unencrypted. Anybody within a
WLAN cell can receive this information, even those who are not associated with an access point. Although this does
not entail any risk for encrypted data connections, the injection of fake management information could severely
disturb the communications within a WLAN cell.
The IEEE 802.11w standard encrypts this management information (protected management frames, PMF), meaning that
potential attackers can no longer interfere with the communications if they don’t have the corresponding key.
Note: As of WPA3, management frames have to be encrypted, so this value is ignored there and is assumed to be set as "Mandatory". For WPA2, this is optional.
- Beacon Protection
-
The IEEE 802.11be (Wi‑Fi 7) standard stipulates the use of beacon protection. This can be configured
here.
Note: The preset "Auto" mode automatically switches Beacon Protection on for all radios that support IEEE 802.11be. To increase compatibility with legacy clients, it may be necessary to switch off Beacon Protection.
- WPA-Rekeying-Cycle
- A 48-bit long initialization vector (IV) impedes attackers in their attempts to calculate the WPA key. WPA also introduced the use of a new key for every data packet (per-packet key mixing and re-keying). The actual key, consisting of the IV and WPA key, is only repeated every 16 million packets. In high-traffic WLANs, the key is repeated only after several hours. To avoid repetition of the key, WPA automatically renegotiates the key at regular intervals. This avoids the repetition of the actual key. Here you configure the time in seconds after which the access point performs rekeying when operating a version of WPA. The standard value is "0" and the key is not negotiated in advance.
- Pre-Authentication
- Fast authentication by means of the
Pairwise Master Key (PMK) only works if the WLAN client was logged on to the access point previously. The WLAN
client uses pre-authentication to reduce the time to logon to the access point at the first logon attempt.
Usually, a WLAN client carries out a background scan of the environment to find existing access points that it could
connect to. Access points that support WPA2/802.1X can communicate their pre-authentication capability to any WLAN
clients that issue requests. A WPA2 pre-authentication differs from a normal 802.1X authentication as follows:
- The WLAN client logs on to the new access point via the infrastructure network, which interconnects the access points. This can be an Ethernet connection or a WDS link (wireless distribution system), or a combination of both connection types.
- A pre-authentication is distinguished from a normal 802.1X authentication by the differing Ethernet protocol (EtherType). This allows the current access point and all other network partners to treat the pre-authentication as a normal data transmission from the WLAN client.
- After successful pre-authentication, the negotiated PMK is stored to the new access point and the WLAN
client.
Important: The use of PMKs is a prerequisite for pre-authentication. Otherwise, pre-authentication is not possible.
- When the client wants to connect to the new access point, the stored PMK significantly accelerates the logon procedure. The further procedure is equivalent to the PMK caching.
- OKC (Opportunistic Key Caching)
- This option enables or disables the opportunistic key caching (OKC). The authentication of WLAN clients via EAP and 802.1X is now standard in company networks, and for public Internet access, too, it is part of the Hotspot 2.0 specification. The disadvantage of authentication via 802.1X is the noticeably longer time between authenticating and connecting due to the exchange of up to twelve data packets between the WLAN client and access point. This may not matter for most applications that only involve exchanging data. However, time-critical applications such as Voice-over-IP rely on fast authentication when moving between WLAN radio cells so as not to impair communications. Various authentication strategies have been established to counteract this, including PMK caching and pre-authentication, although pre-authentication by no means solves all of the problems. For one thing, there is no guarantee that the WLAN client can detect whether the access point is capable of pre-authentication. Also, pre-authentication causes a considerable load on the RADIUS server, because it has to process the authentications of all clients and all access points on the WLAN network. With opportunistic key caching, the management of WLAN client keys is moved to a WLAN controller (WLC) or central switch, which manages all of the access points in the network. When a client authenticates at an access point, the downstream WLC, which acts as the authenticator, performs the key management and returns the PMK to the access point for forwarding to the client. If the client moves to another cell, it uses this PMK and the MAC address of the new access point to calculate a PMKID, and it sends this to the new access point in the expectation that OKC is enabled (i.e. "opportunistic"). If the access point is unable to handle the PMKID, it negotiates a regular 802.1X authentication with the client. A LANCOM access point is even able to perform OKC if the WLC is temporarily unavailable. In this case it stores the PMK and sends it to the WLC, once available again. The WLC then sends the PMK to all of the access points in the network so that the client can continue to use OKC when moving between cells. In networks managed from the LANCOM Management Cloud (LMC) or networks from standalone access points, the PMKs are transmitted via the IAPP protocol. In LMC-managed networks, the IAPP is configured automatically. In networks made up with standalone access points, you have to ensure that the PMK-IAPP secret is configured and identical on every access point in the network.
- WPA2-Key-Management
-
Here you specify which standard the WPA2
key management should follow. Possible values:
- Standard
- Enables key management according to the IEEE 802.11i standard without Fast Roaming and with keys based on SHA‑1. Depending on the configuration, the WLAN clients in this case must use opportunistic key caching, PMK caching or pre-authentication.
- Fast roaming
-
Enables fast roaming according to the IEEE 802.11r standard. See also Fast roaming.
Note: Fast roaming is possible between devices based on LCOS and LCOS LX.
- Standard+Fast-Roaming
- Combination of standard and fast roaming
Important: Although it is possible to make multiple selections, this is advisable only if you are sure that the clients attempting to login to the access point are compatible. Unsuitable clients may refuse a connection if an option other than Standard is enabled.
- SAE/OWE groups
-
Contains the selection of the available Diffie-Hellman groups used by the protocol partners to create a key for
exchanging data. The available groups use elliptical curves.
The authentication method SAE (Simultaneous Authentication of Equals) used by WPA3 uses these methods together with
AES to generate a cryptographically strong key.
- DH-19
- 256-bit random ECP group
- DH-20
- 384-bit random ECP group
- DH-21
- 521-bit random ECP group
- PMK-IAPP-Secret
- This passphrase is used to implement encrypted opportunistic key caching. This is required to use Fast Roaming over IAPP. Each interface must be assigned an individual IAPP passphrase in the WLAN connection settings. This is used to encrypt the pairwise master keys (PMKs). Access points that share a matching IAPP passphrase (PMK-IAPP secret) are able to exchange PMKs between one another and ensure uninterrupted connections. You should therefore ensure that this passphrase is identical on all of the access points that should operate fast roaming.
- RADIUS-Server-Profile
- Here you configure the RADIUS server profile used when operating 802.1X. No input is required when using PSK-based encryption methods. The profiles are created under RADIUS.
Note on WLAN encryption in the 6 GHz band
Since the 6 GHz band is a completely new frequency band, backwards compatibility with older clients is not necessary. Similarly, outdated security methods are not supported. Specifically, this means
- that network encryption is exclusively based on WPA3. Accordingly, no transition mode or mixed mode such as WPA2/3 is available.
- Using Enhanced Open for "open" networks (which thus offer encryption of the transmitted data). It is no longer possible to use open, unencrypted SSIDs.
- Protected Management Frames are mandatory
The conditions mentioned above can be set in the LCOS LX configuration. If an explicit configuration is not desired or possible (e.g. with mixed operation of the same SSID on several bands, which is a common application), the following adjustments are made dynamically by LCOS LX as soon as an SSID on the 6 GHz band is to be used:
- WPA versions <3 are automatically switched to WPA3
- Enhanced Open is enabled for open networks
- Protected Management Frames is activated
This makes it possible to continue using existing encryption profiles and to use a common configuration for an SSID that is also to be broadcast on 6 GHz. These settings are dynamically adjusted during operation, and there is no change to the configuration stored in the device.
