In this table, you configure the IKEv2 connections to VPN partners.
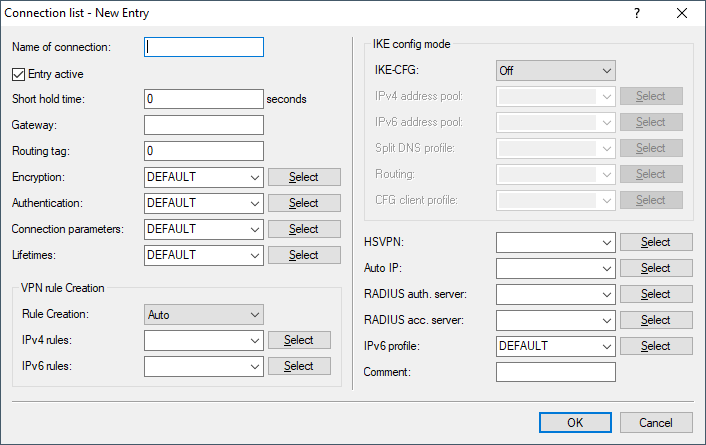
- Name of connection
- Contains the name of the connection to the remote station.
- Entry active
- Enables or disables the connection to this VPN peer.
- Short hold time
- Specifies the hold time in seconds for which the device stays connected if there is no data flow.
- Gateway
- Contains the address (IPv4, IPv6 or FQDN) of the VPN partner. If the value is left blank, there is no additional check of the IP address of the other party. This is required if the remote site has a dynamic IP address, for example. If you specify a FQDN, you can use a suffix to control the DNS resolution. See also Configuration option for IPv4/IPv6 resolution with DNS resolutions.
- Routing tag
- Contains the routing tag for this VPN connection.
- Encryption
- Specifies the encryption used for the VPN connection. The corresponding entry is located in the Encryption table.
- Authentication
- Specifies the authentication method used for the VPN connection. The corresponding entry is located in the Authentication table.
- Connection parameters
- Specifies the general parameters used for the VPN connection. The corresponding entry is located in the Connection parameters table.
- Validity period
- Specifies the lifetime of the key used for the VPN connection. The corresponding entry is located in the table .
- VPN rule creation
- Rule creation
- Specifies how VPN rules are created.
Possible values:
- Automatic
- The local intranet serves as the source network (private IP address range that the local VPN gateway itself belongs to). For automatically generated VPN rules, the target networks are those network ranges that have a remote VPN gateway set as their router. When two simple local networks are connected, the automatic VPN can interpret the necessary network relationships from the IP address range in its own LAN and from the entry for the remote LAN in the IP routing table.
- Manual
- Rules are created for the network relationships in the same way as rules are defined manually for IPv4 or IPv6.
- IPv4-Rules
- Specifies which IPv4 rules apply to this VPN connection. The IPv4 rules are located in the table .
- IPv6-Rules
- Specifies which IPv6 rules apply to this VPN connection. The IPv6 rules are located in the table .
- IKE config mode
- IKE-CFG
- Specifies the IKEv2 config mode of this connection for RAS dial-ins.
Possible values are:
- Off: IKEv2 config mode is disabled
- Server: The router distributes configuration parameters (such as addresses or the DNS server) to VPN clients. The parameters to be distributed are configured in the IPv4 or IPv6 address pool.
- Client: The router requests the server for configuration parameters (e.g. addresses or the DNS server).
- IPv4 address pool
- IPv4 addresses and DNS server for dial-in access in the IKE CFG mode Server.
- IPv6 address pool
- IPv6 addresses and DNS server for dial-in access in the IKE CFG mode Server.
- Split DNS profile
- Name of the Split DNS profile. The split DNS profile is only active if IKE-CFG is set to the value Server.
- Routing
- Specifies the routes that the remote site should transmit dynamically via IKE-CFG mode. This function is only available in the IKEv2 CFG mode for the client and server. The routes for IPv4 and IPv6 connections are located in the tables .
- CFG client profile
- Select a CFG client profile that you created under CFG client profile. This profiles specifies whether the device in the role CFG-Mode client should request an address from the CFG-Mode server.
- HSVPN
-
High Scalability VPN (HSVPN)
In SD-WAN scenarios where branches connect to one or more central sites, there are usually several logical networks that need to be securely separated from one another (e.g. for payment transactions, inventory management, or a hotspot) by means of VLAN and ARF. These local networks were previously connected to the central site either as "stacked" tunnels, i.e. PPTP or L2TP within a VPN tunnel, or as individual IPsec VPN tunnels. However, these architectures do not scale well with large numbers of branches and ARF networks. For example, in an architecture with one tunnel per ARF network, 1,000 branches and 8 ARF networks results in a total of 8,000 tunnels. Stacked tunnels have performance and MTU restrictions due to the protocol overhead.
Figure 1. LANCOM HSVPN scenario for SD-WANThe new architecture LANCOM HSVPN ("LANCOMHigh Scalability VPN") solves these challenges. With HSVPN, packets from ARF networks within an IPsec tunnel are marked with an ARF tag and transported in the VPN tunnel without overhead. This layer-2 based tagging method corresponds to the VLAN layer-3 approach and provides the same level of security. As fewer tunnels are required overall, tunnel establishment times are improved, especially in case of failover. Also, no major restrictions apply with regard to MTU. The following configuration steps are necessary:
- Creating the individual ARF networks
- Creating an IKEv2 tunnel
- The allowed ARF networks are configured as a tag list in the HSVPN configuration profile of the IKEv2 tunnel (HSVPN profiles)
- For the desired ARF networks, corresponding routes must be created through the HSVPN tunnels.
- Classic site-to-site VPN
- CFG mode with IKEv2 routing, where routes and routing tags are transmitted
- Multicast routing is currently not supported over HSVPN. This requires a separate VPN tunnel for multicast.
- OSPF over HSVPN is not supported
- Auto-IP
- Using the Auto-IP parameter, a VPN central site can transmit the IP address of the Dynamic Path Selection measurement target to a VPN branch. For this purpose, the Auto-IP parameter is configured at the central site. At the branch, the measurement target has to be set (IPv4 as 0.0.0.0 or IPv6 as ::) in order for the branch to automatically take over the measurement target from the central site. Refers to the relevant Auto-IP profile, which you set up under IKEv2-Auto-IP-Profile.
- RADIUS auth. server
- Specifies the RADIUS server for the VPN peer authorization. You configure the RADIUS server for IKEv2 under under Extended settings.
- RADIUS acc. server
- Specifies the RADIUS server for the VPN peer accounting. You configure the RADIUS server for IKEv2 under under Extended settings.
- IPv6 profile
- This entry specifies the name of the IPv6 WAN profile. Leaving this entry blank causes IPv6 to be disabled for this interface. The IPv6 remote sites are configured under .
- Comment
- Enter a descriptive comment here.
