Identity list
Use this table to collect other remote identities into a group.
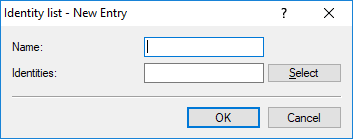
- Name
- Contains the unique name of this entry.
- Identity
- Lists the other identities that are collected into this group. Configure the identities under Identities.
Identities
Use this table to configure additional remote identities. You select this name when grouping remote identities in the Identity list.
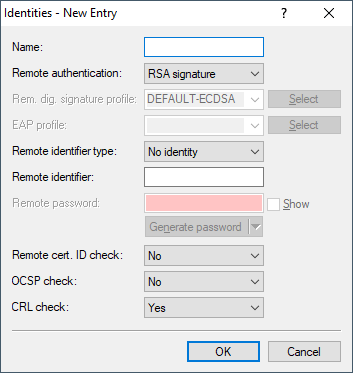
- Name
- Contains the unique name of this entry.
- Remote authentication
- Sets the authentication method for the remote identity.
- Rem. dig. signature profile
- If the Remote authentication is set to "Digital signature", enter the name of the remote digital signature profile here.
- Remote identifier type
- Displays the ID type that the device expects from the remote identifier. The device interprets the entry under "Remote identifier" accordingly. Possible entries are:
- No identity: The device accepts any ID from the remote device. The device to ignores entries in the "Remote identifier" field.
- IPv4 address: The device expects an IPv4 address as the remote ID.
- IPv6 address: The device expects an IPv6 address as the remote ID.
- Domain name (FQDN): The device expects a domain name as the remote ID.
- E‑mail address (FQUN): The device expects an e‑mail address as the remote ID.
- ASN.1 Distinguished Name: The device expects a distinguished name as the remote ID.
- Key ID (group name): The device expects the group name as the remote ID.
- Remote identifier
- Contains the remote identity. The significance of this entry depends on the setting under "Remote identifier type".
- Remote password
- Contains the password of the remote identity.
- Remote certificate ID check
- This option determines whether the device checks that the specified remote identity is included in the received certificate.
- OCSP check
- With this setting you enable the Online Certificate Status Protocol (OCSP), which checks the validity of the remote station's certificate in real time. In order to use the OCSP check for individual VPN connections, you must first enable the global OCSP client for VPN connections and then create profile lists of the valid certificate authorities used by the device to perform the real-time check.
Important: Please note that the check via OCSP only checks the locking status of a certificate, but it does not check the mathematical correctness of its signature, validity period, or other usage restrictions.
- CRL check
-
This setting enables the checking of an X.509 certificate by certificate revocation list (CRL), which checks the validity of
the remote station's certificate.
Important: You should only switch this off if you are checking by other means, e.g. with OSCP.
EAP profiles
This table is used to configure EAP profiles. You select this during authentication if you set the remote authentication method to EAP.
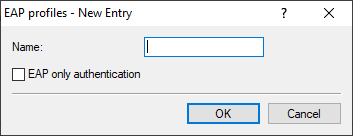
- Name
- Give this EAP profile a name that can be used to reference it.
- EAP-only authentication
- Optionally allows mutual authentication of remote sites within the EAP. Authentication outside the EAP is then not required. See also RFC 5998
Password rules
- Enforce preshared key rules
- This entry gives you the option to disable or enable password-rule enforcement. The following rules apply to the preshared keys (PSK) for IKEv2:
- The length of the password must be at least 32 characters.
- The password must contain at least 3 of the 4 character classes, i.e. lowercase letters, uppercase letters, numbers, and special characters.
Note: These rules do not apply to PSKs managed and sourced from a RADIUS server.
