Details for the encryption over the logical interface in LANconfig are set under .
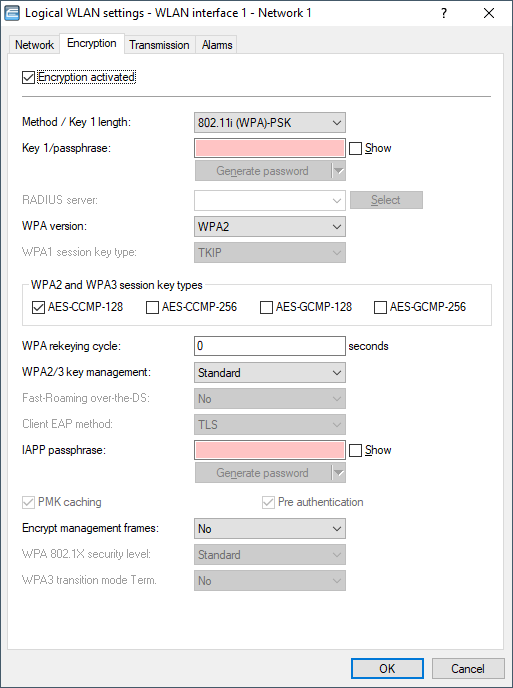
- Enable encryption
- Enable or disable encryption for this WLAN interface.
- Method/key 1 length
- Set the encryption method to be used here. Possible values are:
- 802.11i (WPA)-PSK
- Encryption according to the 802.11i standard offers the highest security. The 128-bit AES encryption used here offers security equivalent to that of a VPN connection. Select this setting if no RADIUS server is available and authentication is based on a pre-shared key.
- 802.11i (WPA)-802.1X
- Select this option if authentication is performed by a RADIUS server. When using this setting, additionally ensure that the RADIUS server is configured in the 802.1X settings.
- WEP 152, WEP 128, WEP 64
- Encryption according to the WEP standard with key lengths of 128, 104 or 40 bits respectively. This setting should only be used if the WLAN client does not support the modern methods.
- WEP 152-802.1X, WEP 128-802.1X, WEP 64-802.1X
- Encryption according to the WEP standard with key lengths of 128, 104 or 40 bits respectively, and with additional authentication via 802.1X/EAP. This setting is also only to be recommended when the hardware used by the WLAN client does not support the 802.11i standard. The 802.1X/EAP authentication offers a higher level of security than WEP encryption alone.
- Enhanced Open
- Until now, hotspots were mainly operated without encryption, meaning that the data transmitted over the wireless interface was open to inspection. Also, the widespread practice of securing a hotspot with WPA2-PSK and publicly posting the shared key provides limited security. Since WPA2-PSK does not provide Perfect Forward Secrecy, an attacker who knows the key can use it to decrypt recordings of data traffic. The Enhanced Open method minimizes these risks. Clients that support this method use encrypted communication to prevent other users in the same radio cell from eavesdropping on their communications. The threat of a man-in-the-middle attack remains, but the risk is much lower than when using an unencrypted open hotspot. Just set the encryption method. That is all you need to do to encrypt communications for clients that support this method. To use Enhanced Open with the Public Spot, also see Setting up a secure hotspot with Enhanced Open.
- Enhanced Open Transitional
- The Enhanced Open Transition mode allows connections to clients that support Enhanced Open and also to those that do not yet support Enhanced Open. With the transition mode in operation, the regular Enhanced Open SSID is operated in parallel to an unencrypted/open SSID with the same name and otherwise identical settings.
Note: A prerequisite for this is that at least one other SSID is available and unused on the selected radio module. Depending on the device, a total of 15 or 16 SSIDs are available per radio module. If no SSID is available, both the Open Transition SSID and the actual Enhanced Open SSID will not be activated.
- Key 1/passphrase
- In line with the encryption method activated, you can enter a special WEP key for the respective logical WLAN interface or a passphrase when using WPA-PSK:
- The passphrase, or the "password" for the WPA-PSK method, is entered as a string of at least 8 and up to 63 ASCII characters. Important: Please be aware that the security of this encryption method depends on the confidential treatment of this passphrase. Passphrases should not be made public to larger circles of users.
- The WEP key 1, that applies only to its respective logical WLAN interface, can be entered in different ways depending on the key length. Rules for entering the keys can be found in the description of the WEP group key.
- The passphrase, or the "password" for the WPA-PSK method, is entered as a string of at least 8 and up to 63 ASCII characters.
- RADIUS server
- If you operate RADIUS for the central administration of accounts and access credentials in your wireless network, then the access point forwards requests for the authorization and accounting to the RADIUS server by default. If you are using a WLAN controller for access point management, then the controller can forward RADIUS requests from all of these access points to the RADIUS server. In some cases, the operator of access points or WLAN controllers may wish to use a different RADIUS server for each logical wireless network (SSID). This may be the case, for example, when multiple customers share the same technical WLAN infrastructure but use their own authentication systems (e.g. with Wireless as a Service – WaaS). In these cases, you have the option to choose a separate RADIUS profile for each logical WLAN (i.e. each SSID). The RADIUS profile contains all of the necessary information to use the appropriate RADIUS server, including the optional backup solution. If you select an authentication method based on the IEEE 802.1X standard under Method/Key 1 length, you specify the profile of a RADIUS server here.
- WPA-Version
- WPA version for encryption offered by the access point to the WLAN clients.
- WPA1
- WPA2 only
- WPA2
- WPA2 only
- WPA1/2
- WPA1 and WPA2 in one SSID (radio cell)
- WPA2/3
- WPA2 and WPA3 in one SSID (radio cell)
- WPA3
- WPA3 only
- WPA1/2/3
- WPA1, WPA2 and WPA3 in one SSID (radio cell)
- WPA1 session key type
- If '802.11i (WPA)-PSK' has been entered as the encryption method, the procedure for generating a session or group key for WPA1 can be selected here:
- AES
- The AES method will be used.
- TKIP
- The TKIP method will be used.
- AES/TKIP
- The AES method will be used. If the client hardware does not support the AES method, TKIP will be used.
- WPA2 and WPA3 session key types
- Here you select the methods that should be offered for generating the WPA2 or WPA3 session or group keys. The following Advanced Encryption Standard (AES) methods can be offered: AES-CCMP-128, AES-CCMP-256, AES-GCMP-128, AES-GCMP-256.
- WPA rekeying cycle
- Here you configure the time in seconds after which the access point performs rekeying when operating a version of WPA. By default, the value is set to "0", so there is no renegotiation of the key.
- WPA2/3 key management
- Here you specify the standard to be used for WPA2/3 key management. Possible values are:
- Standard
- Enables key management according to the IEEE 802.11i standard without Fast Roaming and with keys based on SHA-1. Depending on the configuration, the WLAN clients in this case must use opportunistic key caching, PMK caching or pre-authentication.
- Fast roaming
- Enables fast roaming as per 802.11r
- SHA256
- Enables key management according to the IEEE 802.11w standard with keys based on SHA-256.
- Combinations of these three settings
- Activates a corresponding combination.
Important: Although it is possible to make multiple selections, this is advisable only if you are sure that the clients attempting to login to the AP are compatible. Unsuitable clients may refuse a connection if an option other than Standard is enabled. - Fast-Roaming over-the-DS
- With Fast Roaming over-the-DS (Distribution System) you can activate an option of the IEEE 801.11r standard, which takes advantage of the LAN connection between the access points. The roaming request is sent to the access point that the client is connected to. The AP forwards the request to the new access point and the swap is performed. This means significantly faster roaming speeds than possible with the usual "over-the-air fast transition", which is a big benefit to real-time applications such as VoIP.
- Client EAP method
- In WLAN client operating mode, APs can authenticate themselves to another AP using EAP/802.1X. To activate the EAP/802.1X authentication in client mode, the client EAP method is selected as the encryption method for the first logical WLAN network.
Important: Note that the selected client EAP method must match the settings of the access point that the AP is attempting to log onto.Important: In addition to setting the client EAP method, also be sure to observe the corresponding setting for the WLAN client operation mode. The client EAP method setting has no function on logical WLAN networks other than WLAN 1.
- IAPP passphrase
- This passphrase is used to implement encrypted opportunistic key caching. See Opportunistic key caching (OKC).
- PMK caching
- When establishing a connection from a WLAN client to an AP operating with 802.1X-authentication, the two stations negotiate a shared key, known as the Pairwise Master Key (PMK), for the subsequent encryption. In applications with mobile WLAN clients (laptops in large offices, moving objects with WLAN connections in the industrial sector, smartphones), the WLAN clients often switch between the APs they use to access the WLAN network. And although WLAN clients roam back and forth between different APs, in most cases these tend to be the same ones. APs typically save a negotiated PMK for a certain period of time. WLAN devices in WLAN client mode also store PMKs. As soon as a WLAN client starts a login procedure for which a connection already existed, the WLAN client can directly transfer the existing PMK to the AP. In this way, the two remote stations skip the PMK negotiation phase while establishing the connection, and the WLAN client and AP establish the connection much faster.
- Pre-authentication
-
Fast authentication by means of the Pairwise Master Key (PMK) only works if the WLAN client was logged on to the AP previously. The WLAN client uses pre-authentication to reduce the time to logon to the AP at the first logon attempt.
Usually, a WLAN client carries out a background scan of the environment to find existing APs that it could connect to. APs that support WPA2/802.1X can communicate their pre-authentication capability to any WLAN clients that issue requests. A WPA2 pre-authentication differs from a normal 802.1X authentication as follows:
- The WLAN client logs on to the new AP via the infrastructure network, which interconnects the APs. This can be an Ethernet connection or a WDS link (wireless distribution system), or a combination of both connection types.
- A pre-authentication is distinguished from a normal 802.1X authentication by the differing Ethernet protocol (EtherType). This allows the current AP and all other network partners to treat the pre-authentication as a normal data transmission from the WLAN client.
- After successful pre-authentication, the negotiated PMK is stored to the new AP and the WLAN client. Important: The use of PMKs is a prerequisite for pre-authentication. Otherwise, pre-authentication is not possible.
- When the client wants to connect to the new AP, the stored PMK significantly accelerates the logon procedure. The further procedure is equivalent to the PMK caching.
Important: On the client side, the number of concurrent pre-authentications is limited to four. This minimizes the network load on the central RADIUS server in network environments with large numbers of APs. - Encrypt management frames
- By default, the management information transmitted on a WLAN for establishing and operating data connections is unencrypted. Anybody within a WLAN cell can receive this information, even those who are not associated with an access point. Although this does not entail any risk for encrypted data connections, the injection of fake management information could severely disturb the communications within a WLAN cell.
The IEEE 802.11w standard encrypts this management information (protected management frames, PMF), meaning that potential attackers can no longer interfere with the communications if they don’t have the corresponding key.
Note: As of WPA3, management frames must be encrypted. For WPA2, this is optional.
- WPA 802.1X security level
-
WPA-3 additionally features support for the Commercial National Security Algorithm (CNSA ) Suite B cryptography, which is an optional part of WPA3-Enterprise for high-security environments. Suite B ensures that all links in the encryption chain match with one another. Suite B forms classes of bit lengths for hashed, symmetric, and asymmetric encryption in order to provide suitable levels of protection. For example, an SHA-2 hash with 256 bits matches AES with 128 bits. Where Suite B is operated, the support of all other combinations is expressly excluded. Consequently, the encryption chain consists of links of equal strength.
Note: Further information on CNSA Suite B can be found at the following link: CNSA algorithm suite factsheetThe switch WPA 802.1X security level under is used to enable the optional Suite B encryption. With "Suite B 192 bits" support enabled, the following EAP cipher suites are enforced:
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
Note: Other cipher suites can no longer be used. Also enforced are a minimum key length of 3072 bits for the RSA and Diffie-Hellman key exchange, as well as 384 bits for the ECDSA and ECDHE key exchange. The session key type AES-GCMP-256 is also enforced.Important: If these cipher suites are not supported by the WLAN clients or the remaining infrastructure (e.g. the RADIUS server), then no connection is possible!With "Suite B 128 bits" support enabled, the following EAP cipher suites are enforced:- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
Note: Other cipher suites can no longer be used. Also enforced are a minimum key length of 3072 bits for the RSA and Diffie-Hellman key exchange, as well as 384 bits for the ECDSA and ECDHE key exchange. The session key type AES-GCMP-128 is also enforced.Because the session key types AES-GCMP-128 and AES-GCMP-256 are not supported by all WLAN modules, the use of Suite B cryptography may be limited or impossible, depending on the device type.Important: If these cipher suites are not supported by the WLAN clients or the remaining infrastructure (e.g. the RADIUS server), then no connection is possible!Note: This option is only displayed if the device supports it. - WPA3 Transition Mode Term.
- This setting uses an additional info element to explicitly signal WLAN clients that the WPA3-PSK (SAE) encryption method is supported in the mixed WPA2/3 mode. If the client supports the "Transition Mode Termination" feature, it will always use WPA3-PSK (SAE) to authenticate with this SSID. This prevents a downgrade to WPA2-PSK, which is otherwise also allowed in mixed WPA2/3 mode.
