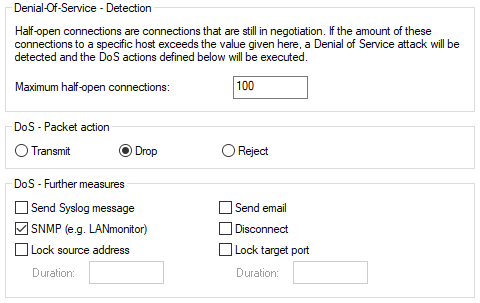
LANconfig:
Command line:
For all permitted accesses, the device explicitly checks the connection state, the source addresses, and the correctness of the fragments. This is performed both for incoming and outgoing packets, since an attack can also be launched from within the local network.
In order to avoid opening a path for DoS attacks due to the incorrect configuration of the firewall, this aspect is configured centrally. Along with the maximum number of half-open connections, the packet action and the available reporting mechanisms, there are further reaction options:
- Disconnection
- The source address is blocked for an adjustable time
- The target port of the scan is blocked for an adjustable time
The following protection mechanisms are always active:
- Address inspection (against IP spoofing)
- Blocking broadcasts into local network (against Smurf, etc.)
