The RADIUS user database is used to enter the user accounts that the RADIUS server can authenticate without any further databases. This database uses the RADIUS server for local requests, also for requests with usernames without a realm.
Important: Please note that the number of users the database can accommodate depends on the model. The
maximum possible number of user accounts can be found in the product description of your device. For devices
without a limit, we recommend an upper limit of max. 2,500 users.
The RADIUS user database is configured via .
- Use the WLAN station table for MAC address requests
-
This parameter specifies whether the WLAN access list is to be used as an information source for the RADIUS
server in the access point. The WLAN access list contains the user name in the form of the MAC address and
the password ("WPA passphrase"). In addition to this access data, the access list provides information
such as bandwidth restriction and association to a specific VLAN.
The WLAN access list can be found under . Up to 512 WLAN clients may be entered here so they can associate with the access point. When
operating in RADIUS server mode, this list can also be used to check on RADIUS clients wanting to register
at other access points. In an installation having several access points, client access authorizations can be
maintained centrally.
Once a WLAN client is logged on after authentication by RADIUS, it remains active until it logs off itself
or is logged off by the RADIUS server. By specifying a recheck cycle [minutes], the RADIUS server can
regularly check whether the WLAN clients logged in are still in the access list. If a WLAN client is removed
from the access list, it remains logged in to the WLAN up to the point when the recheck cycle runs again.
You can adjust the recheck cycle from the CLI under .
Important: A recheck cycle of '0' disables regular checking. WLAN clients remain logged in until they log themselves out.
- Auto cleanup user table
-
Enabling this option causes expired user accounts to be deleted from the user table automatically. This
considers user accounts with validity periods that are absolute and relative.
Note: The device must operate as an accounting server and as an authentication server in order to process accounts with a relative validity period and accounts with a time or volume budget.
With User table you define the entries for local requests.
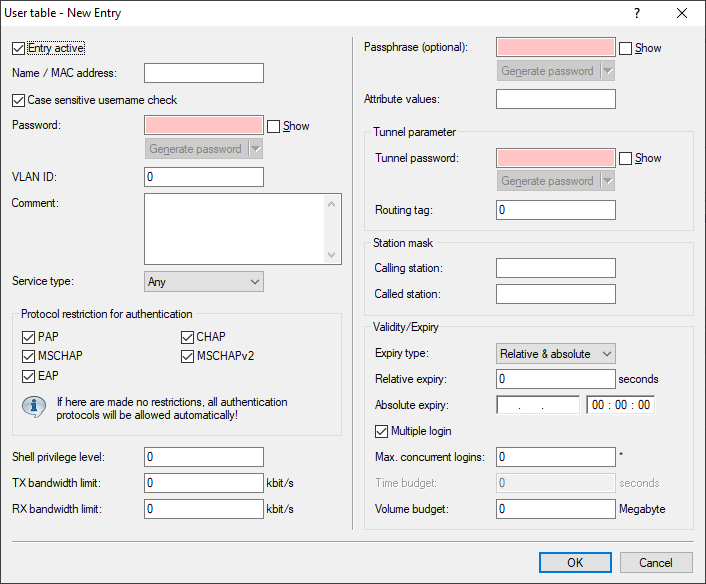
- Entry active
- Using this option, you specifically enable or disable an individual RADIUS user account. This makes it possible to disable individual accounts temporarily without deleting the entire account, for example.
- Name / MAC address
-
Enter the name or MAC address of the user
Note: The MAC address is used in combination with the passphrase for LEPS-MAC authentication.
- Cast-sensitive user name check
- When enabled, the RADIUS server distinguishes between uppercase and lowercase. "User12345" and "user12345" are therefore two different users.
- Password
- User password.
- VLAN-ID
- This option allows a certain VLAN ID to be assigned to the user on successful authorization. A value of 0 means that no VLAN ID is assigned to the user.
- Comment
- Additional information about the user.
- Service type
- The service type is a special attribute of the RADIUS protocol, which the NAS (Network Access Server)
transmits with the authentication request. The request will only receive a positive response if the requested
service type fits the service type of the user account. Possible values include:
- Any: The service type can be any type.
- Framed: For checking WLAN MAC addresses via RADIUS or IEEE 802.1X.
- Login: For Public Spot authentications.
- Authentication only: For RADIUS authentication of dialup peers via PPP.
- and various others that are defined by the RADIUS protocol.
Important: Please note that, depending on the device, the number of entries can be limited with the service type Any or Login. If your device is able to manage a total of 64 Public Spot users, for example, the LANconfig rejects any after 64. User account with the service type Any/Login requires the creation of additional user accounts with these service types. - Protocol restriction for authentication
- This option limits the selection of authentication methods allowed for the user. Possible values are:
- PAP
- The NAS passes the user name and password. The RADIUS server searches its data sets for an entry matching the user name, compares the password, and responds with a RADIUS accept or RADIUS reject.
- CHAP
- The NAS passes the user name, the CHAP challenge and characteristics of the password (but not the password itself). The RADIUS server searches its data sets for an entry matching the user name; it uses the associated password and the CHAP challenge from the NAS to compute the CHAP response. If this computed response and the answer sent by the client via the NAS correspond, then the RADIUS server sends a RADIUS accept; otherwise it sends a RADIUS reject.
- MSCHAP
- The NAS passes the user name, the MS-CHAP challenge and the MS-CHAP password characteristics. The method continues in the same way as CHAP, although the responses are computed with the MS-CHAP algorithm (RFC 2433).
- MSCHAPv2
- The NAS passes the user name, the MS-CHAP challenge and the MS-CHAPv2 response. The method continues in the same way as CHAP and MS-CHAP, although the responses are computed with the MS-CHAPv2 algorithm (RFC 2759). Furthermore the RADIUS server transmits an MS-CHAPv2 confirmation once the authentication was successful. This confirmation contains the server's response to the client's challenge, so enabling a mutual authentication.
- EAP
- The NAS passes the user name and an EAP message. Unlike the methods outlined above, EAP is not stateless, i.e. in addition to sending an access accept or access reject, the RADIUS server issues its own challenge before authentication is completed. EAP itself is a modular authentication protocol that accommodates various methods of authentication.
- Shell privilege level
- Vendor-specific RADIUS attribute to communicate the privilege level of the user in a RADIUS-Accept (default: 0).
- TX bandwidth limit
- Bandwidth limitation for sending data.
- RX bandwidth limit
-
Bandwidth limitation for receiving data
Important: The bandwidth limitation for sending and receiving applies regardless of the interface used (LAN and WLAN).
- Passphrase
-
The respective WPA passphrase assigned to the registered user. This enables a LAN-connected device to
operate as a central RADIUS server and benefit from LEPS-MAC (LANCOM Enhanced Passphrase Security MAC).
The configuration of LEPS-MAC involves the assignment of an individual passphrase to the MAC address of
each client that is approved for the WLAN. This is done either with an entry in the list under (see LANCOM Enhanced Passphrase Security MAC (LEPS-MAC)) or in the RADIUS server. One entry is generated per MAC
address—from the point of view of the RADIUS server, the MAC address is therefore a user. It is also
necessary to activate the MAC filter under , i.e. data will be transmitted for the WLAN clients entered here.
Important: The passphrase can be a string of 8 to 64 characters. We recommend that the passphrases consist of a random string at least 32 characters long.Note: If you are storing client-specific passphrases in the user table of a RADIUS server, a LAN-based device can serve as the central RADIUS server and take advantage of LEPS-MAC.
- Framed IP Address
- Defines the Framed IP Address attribute (according to RFC 2865, attribute type 8) for this RADIUS user.
- Framed IPv6 Address
- Defines the Framed IPv6 Address attribute (according to RFC 6911, attribute type 168) for this RADIUS user.
- Framed IPv6 Prefix
- Defines the Framed IPv6 Prefix attribute (according to RFC 3162, attribute type 97) for this RADIUS user.
- Delegated IPv6 Prefix
- Defines the Delegated IPv6 Prefix attribute (according to RFC 4818, attribute type 123) for this RADIUS user.
- Attribute values
- Here you can assign user-defined
values to RADIUS attributes. The individual name-value pairs must have the form <Name>=<Value>,
and they are separated by semicolons.
<Name> identifies the RADIUS attribute by its name or number. The associated attribute names can be
found in the corresponding RADIUS RFCs. Attribute names can be abbreviated as long as the identifiers are
unequivocal.
As the number of characters is limited, the name can abbreviated. The abbreviation must be unique, however. Examples:
- NAS-Port=1234 is not allowed, because the attribute is not unique (NAS-Port, NAS-Port-Id or NAS-Port-Type).
- NAS-Id=ABCD is allowed, because the attribute is unique (NAS-Identifier).
- %n – replaced by the configured device name.
- %e – replaced with the serial number of the device as displayed in the device system info.
- %% – replaced by a single % character.
- %{name} – replaced by the original value of the corresponding RADIUS attribute. Any new / re-definitions within this attribute list are ignored. The identifier can be truncated as long as it remains unique.
- Tunnel-Password
- This entry sets the connection password for each user.
- Routing tag
- Specify the routing tag for this connection.
- Calling station
- This mask limits the validity of the entry to certain IDs transmitted by the calling station (WLAN client). When authenticating via 802.1X the calling station's MAC address is transmitted in ASCII format (capital letters only) with a hyphen separating pairs of characters (for example, "00-10-A4-23-19-C0").
- Called station
- This mask limits the validity of the entry to specified IDs as transmitted by the called station (BSSID and SSID of the access point). When authenticating via 802.1X the called station's MAC address (BSSID) is transmitted in ASCII format (capital letters only) with a hyphen separating pairs of characters. The SSID is appended using a colon as a separator (e.g., "00-10-A4-23-19-C0:AP1").
- Expiry type
- This option specifies the type of the validity period of the user account. Possible values are:
- Relative & absolute:
- Relative
- Absolute
- Never
- Relative expiry
- Validity period in seconds from the initial successful login.
- Absolute expiry
- Validity period in hours, minutes and seconds from a certain date.
- Multiple login
- Activates the option for the client to register more than once
- Maximum number
- Maximum number of concurrent logins by the client
- Time budget
- Specifies the time in seconds available to the client if Multiple login is not enabled.
- Volume budget
- Specifies the data volume available to the client.
