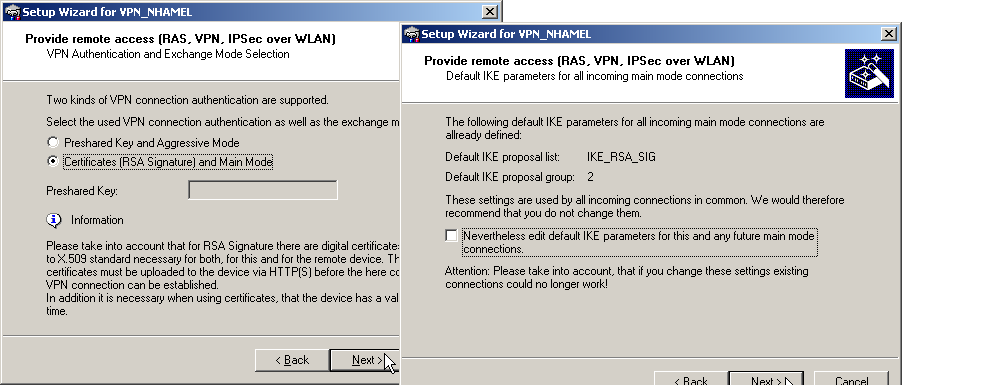
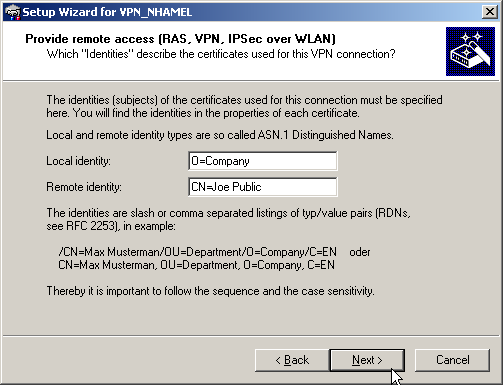
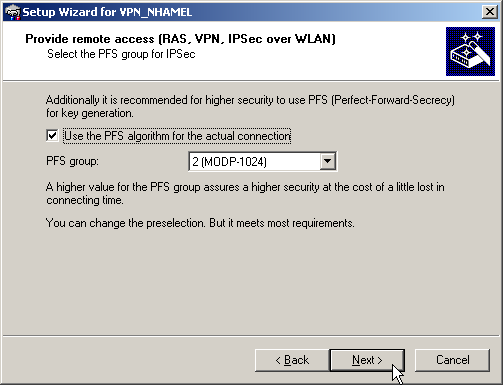
RAS connections that support certificates can be set up for the LANCOM Advanced VPN Client or for any other VPN client with user-defined parameters. The LANCOM Standard VPN Client does not support certificates.
Note: Various parameters are requested depending on the choice of client or the options. This description shows all of the possible
Wizard dialogs, some of which may not necessarily be relevant for your application.