When dialling in, the identity of computers that use varying IP addresses is unknown at the initial stages of the IKE negotiation (Phase 1), so communication is facilitated by using default values for IKE proposal lists and IKE proposal groups. During negotiation, the identity is communicated and this is used to determine the parameters for phase 2 (IPSec proposal list and PFS group). For this to occur, every single user must be entered individually into the VPN router configuration.
With certificate-based RAS, the identity is communicated via the certificate. To avoid having to make individual user entries in the router configuration, common parameters for phase 2 can be defined for all users who are identified by certificate. All the user requires for simplified RAS is a valid certificate with a signature from the publisher of the root certificate in the device. Furthermore, the parameters used by the client during dial-in must agree with the default values in the VPN router.
This function has to be activated to configure the simplified dial-in. The default parameters can be altered according to requirements.
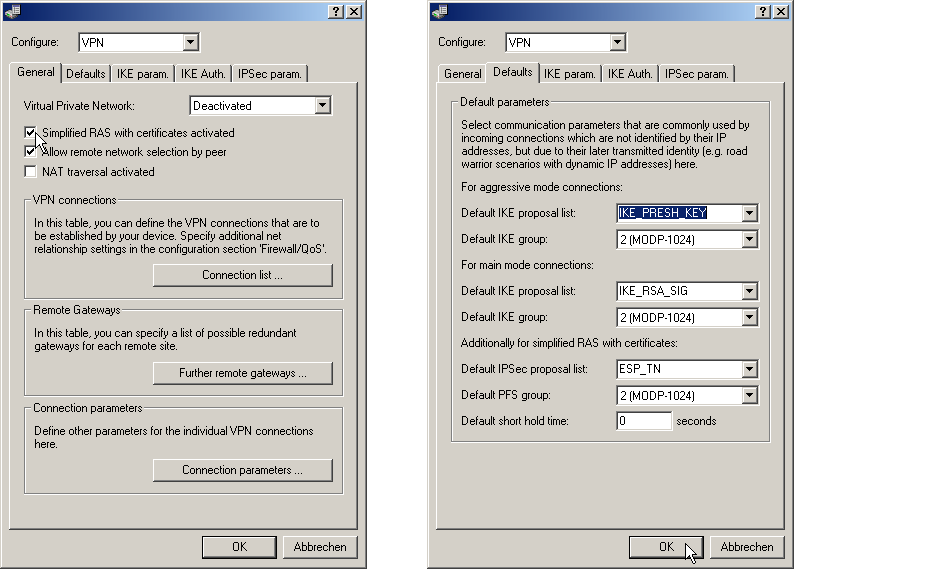
LANconfig: VPN / General and VPN / General / Defaults
WEBconfig: LCOS menu tree / Setup / VPN