If an event occurred that had to be logged in either way, i.e. a log action was specified with the receipt of a packet, or a report by e-mail, Syslog or SNMP was generated, then this event is held in the logging table.
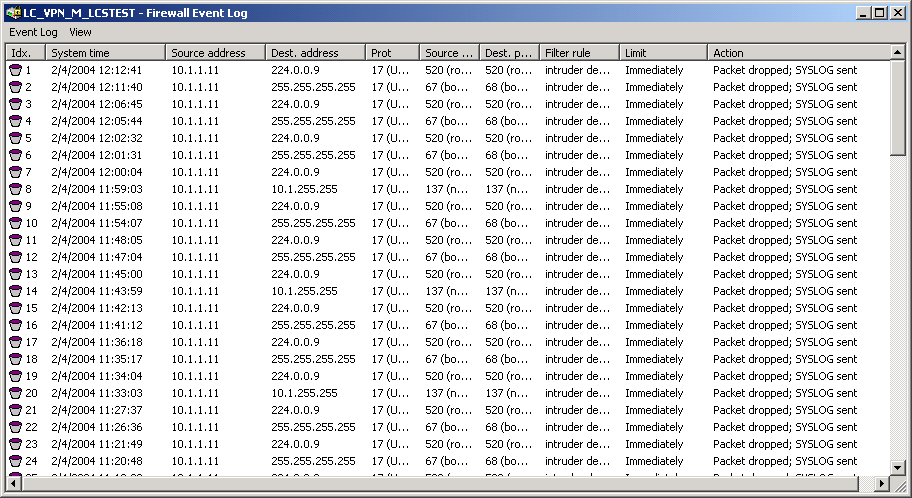
If you call up the logging table via LANmonitor, it looks like the following depiction:
If you call up the logging table via WEBconfig, it looks like the following depiction:
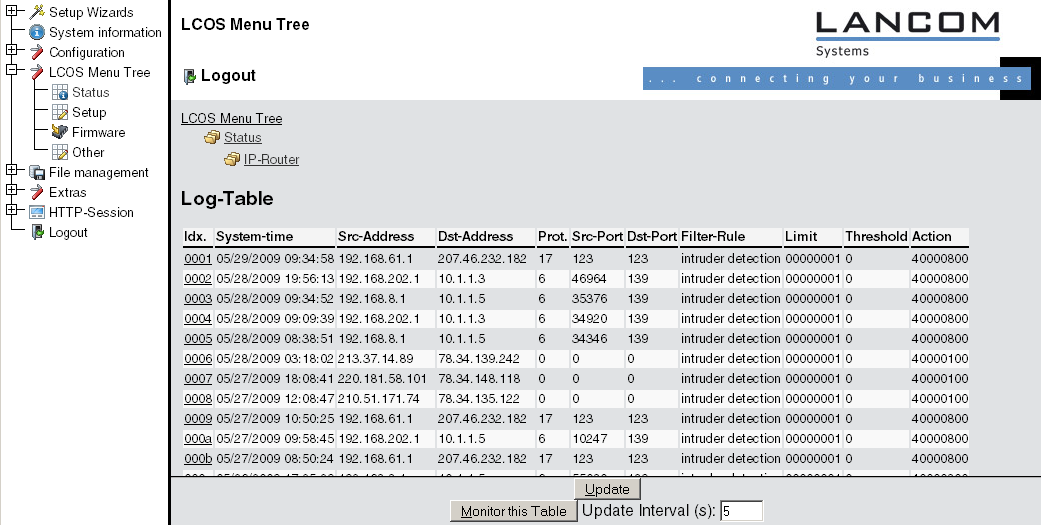
The table contains the following values:
| Element | Element meaning |
|---|---|
| Idx. | Current index (so that the table can be polled also via SNMP) |
| System time | System time in UTC codification (will be transformed on displaying of the table into clear text) |
| Src address | Source address of the filtered packet |
| Dst address | Destination address of the filtered packet |
| Prot. | Protocol (TCP, UDP etc.) of the filtered packet |
| Src-p | Source port of the filtered packet (only with port-related protocols) |
| Dst-p | Destination port of the filtered packet (only with port-related protocols) |
| Filter-Rule | Name of the rule, which has raised the entry. |
| Limit | Bit field, which describes the crossed limit, which has filtered the packet. The following values are defined at present: 0x01 Absolute number 0x02 Number per second 0x04 Number per minute 0x08 Number per hour 0x10 Global limit 0x20 Byte limit (if not set, it concerns a packet-related limit) 0x40 Limit applies only in receiving direction 0x80 limit applies only in transmission direction |
| Threshold | Exceeded limit value of the trigger limit |
| Action | Bit field, which specifies all implemented actions. At present the following values are defined: 0x00000001 Accept 0x00000100 Reject 0x00000200 Connect filter 0x00000400 Internet- (Default route-) filter 0x00000800 Drop 0x00001000 Disconnect 0x00004000 Block source address 0x00020000 Block destination address and port 0x20000000 Send SYSLOG notification 0x40000000 Send SNMP trap 0x80000000 Send email |
Note: All Firewall actions are likewise displayed within the IP router trace. Furthermore, some
LANCOM models have a Firewall LED, which signals each filtered packet.