Currently, users can login to the administration interface of the device by using RADIUS, TACACS+, or the internal user management of the device.
With RADIUS, this is possible over the following connections:
- Telnet
- SSH
- WEBconfig
- TFTP
- Outband
Note: A RADIUS authentication over SNMP is currently not supported.
Note: A RADIUS authentication via LL2M (LANCOM Layer 2 Management protocol) is not supported as LL2M requires plain-text access to the password stored in the LANCOM.
The RADIUS server handles user management with regard to authentication, authorization and accounting (triple-A protocol), which greatly simplifies the management of admin accounts in large network installations with multiple routers.
Authentication via a RADIUS server is conducted as follows:
- On login, the LANCOM sends the user credentials to the RADIUS server in the network. The necessary server data are in stored in the LANCOM.
- The server checks the credentials for their validity.
- If the credentials are invalid, it sends the LANCOM a corresponding message and the LANCOM aborts the login process with an error message.
- If the credentials are valid, the server informs the LANCOM that the user has permission of access, and also sends information on the access rights and function rights, so that the user has access only to the corresponding functions and directories.
- If the user's sessions are budgeted by the RADIUS server (accounting section), the LANCOM stores the session data such as start, end, user name, authentication mode and, if available, the port used.
In the LANconfig, you can set the authentication method under .
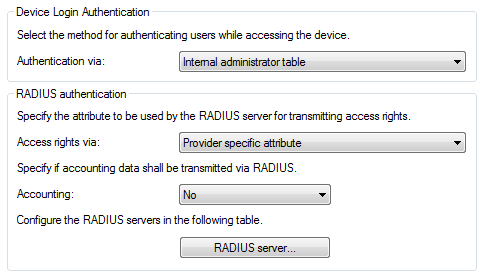
In the section Device login authentication, you choose the method for users to authenticate when accessing the LANCOM administration interface:
- Internal administrator table: The LANCOM handles the user management itself by means of user login name, password, and the assignment of access and function rights.
- RADIUS: User management is handled by a RADIUS server in the network.
- TACACS+: User management is handled by a TACACS+ server in the network.
In the the RADIUS authentication section, you enter the necessary RADIUS server data and additional administrative data.
- Access rights via
- The authorization of the user is stored in the RADIUS server. When a request arrives, the RADIUS server sends the access- and function rights to the LANCOM along with the login data, which then logs in the user with the appropriate privileges.
Access and function rights are usually defined in the RADIUS management privilege level (attribute 136), and the LANCOM simply maps these values to its internal access and function rights. However, some RADIUS servers use this attribute differently, or they may use different, vendor-specific attributes for the authorization. In this situation, the LANCOM is also able to evaluate provider-specific authorizations. Possible values are:
- Provider-specific attribute: The LANCOM processes the provider-specific attribute (default).
- Management privilege level attribute: The LANCOM processes the RADIUS server's management privilege level attribute.
- Accounting
- Here, you specify whether the LANCOM should record the user's session. Possible values are:
- No: The LANCOM does not record any session data (default).
- Yes: The LANCOM records the session data (start, end, user name, authentication mode, port).
- RADIUS server
- This table is used to define the RADIUS server settings.
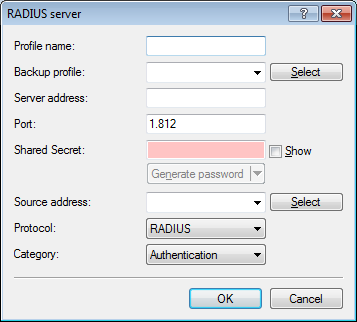
- Profile name: Enter a name for the RADIUS server here.
- Backup profile: Enter the name of the alternate RADIUS server to which the LANCOM forwards its requests if the first RADIUS server is unavailable.Note: The backup server requires an additional entry in the Server table.
- Server address: Enter the IPv4 address of the RADIUS server here.
- Port: Enter the port used by the RADIUS server to communicate with the LANCOM (default: 1812).
- Shared secret: Enter the password for accessing the RADIUS server here, and repeat the entry in the second input field.
- Source address: This is where you can configure an optional sender address to be used by the LANCOM instead of the one that would normally be automatically selected for this target address.
- Protocol: Enter the protocol used by the RADIUS server to communicate with the LANCOM. Possible values are:
- RADIUS (default)
- RADSEC
- Category: Set the category for the RADIUS server. Possible values are:
- Deactivated
- Authentication (default)
- Accounting
- Authentication & accounting