SNMP communities
Administrators of networks with SNMP management systems can precisely control the access rights to various access levels. SNMP of the versions v1 and v2 do this by encoding the access credentials as part of a "community". Authentication is optionally handled
- by the public community (unlimited SNMP read access),
- by a master password (limited SNMP read access),
- or a combination of user name and password, separated by a colon (limited SNMP read access)
.
A community collects certain SNMP hosts into groups, in part so that it is easier to manage them. On the other hand, SNMP communities offer a certain degree of security because an SNMP agent only accepts SNMP requests from participants in a community that it knows.
By default, your device answers all SNMP requests that it receives from LANmonitor or another SNMP management system with the community public. Because this represents a potential security risk, especially with external access, LANconfig gives you the option of defining your own communities.
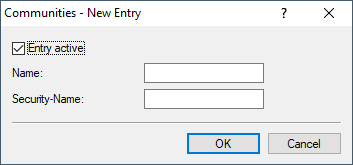
- Entry active
- Activates or deactivates this SNMP community.
- Name
- Enter a descriptive name for this SNMP community.
- Security-Name
- Here you enter the name for the access policy that specifies the access rights for all community members.
For SNMPv1 or SNMPv2c, you force the entry of login data for SNMP read-only access by disabling the public community in the list of the SNMP communities. This setting only allows information about the state of the device, current connections, reports, etc., to be read out via SNMP after the user authenticates at the device. Authorization can be conducted either with the administrator-account access credentials or an access account created for the individual SNMP community.
Disabling the community public has no effect on accessing for other communities created here. An individual SNMP read-only community always provides an alternative access path that is not tied to an administrator account.
Users
Individual users can be granted access to the device in addition to the administrators registered on it. Here you configure the authentication and encryption settings for these users when operating SNMPv3.
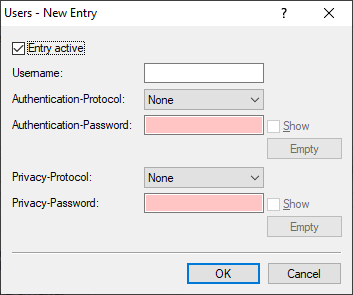
- Entry active
- Activates or deactivates this user.
- User name
- Enter a descriptive name for this user.
- Authentication
-
Specify the method that the user is required to use to authenticate at the SNMP agent. The following options are available:
- None
- Authentication of the user is not necessary.
- HMAC-MD5
- Authentication is performed using the hash algorithm HMAC‑MD5‑96 (hash length 128 bits).
- HMAC-SHA
- Authentication is performed using the hash algorithm HMAC-SHA (hash length 160 bits).
- HMAC-SHA224
- Authentication is performed using the hash algorithm HMAC-SHA‑ 224 (hash length 224 bits).
- HMAC-SHA256
- Authentication is performed using the hash algorithm HMAC-SHA‑ 256 (hash length 256 bits).
- HMAC-SHA384
- Authentication is performed using the hash algorithm HMAC-SHA‑ 384 (hash length 384 bits).
- HMAC-SHA512
- Authentication is performed using the hash algorithm HMAC-SHA‑ 512 (hash length 512 bits).
- Authentication password
- Enter the user password necessary for authentication here and repeat it in the box below.
- Encryption
- Specify which encryption method is used for encrypted communication with the user. The following options are available:
- None
- Communication is not encrypted.
- DES
- Encryption is performed with DES (key length 56 bits).
- AES128
- Encryption is performed with AES128 (key length 128 bits)
- AES192
- Encryption is performed with AES192 (key length 192 bits)
- AES256
- Encryption is performed with AES256 (key length 256 bits)
- Privacy password
- Enter the user password required by the encryption here and repeat it in the box below.
Groups
By configuring SNMP groups, it is easy to manage and assign the authentication and access rights of multiple users. By default, the configuration is set up for SNMP access via LANmonitor.
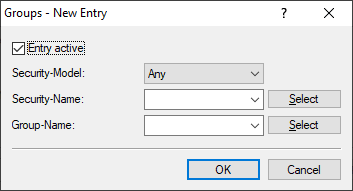
- Entry active
- Activates or deactivates this group.
- Security model
- SNMPv3 introduced the principle of the "security model", so that the SNMP configuration in LCOS LX primarily uses the security model "SNMPv3". However, for compatibility reasons it may be necessary to also take the versions SNMPv2c or even SNMPv1 into account, and to select these as the "security model" accordingly. Select one of the following entries accordingly:
- Any
- Any model is accepted.
- SNMPv1
- Data is transmitted by SNMPv1. Users are authenticated by the community string in the SNMP message only. Communication is not encrypted. This corresponds to the security level "No authentication/No privacy".
- SNMPv2_C
- Data is transmitted by SNMPv2c. Users are authenticated by the community string in the SNMP message only. Communication is not encrypted. This corresponds to the security level "No authentication/No privacy".
- SNMPv3_USM
- Data is transmitted by SNMPv3. Security levels for the user’s authentication and communication are possible, and these levels are activated with the access rights.
- Security-Name
- Here you select a security name you assigned to an SNMP community.
- Group name
- Here you select a group that you want to define under Access rights.
Access rights
This table brings together the different configurations for access rights, security models, and views.
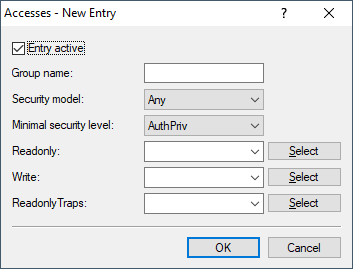
- Entry active
- Activates or deactivates this entry.
- Group name
- Enter a descriptive name for this group.
- Security model
- Activate the appropriate security model here.
- Minimal security level
- Specify the minimum security level for access and data transfer.
- NoAuthNoPriv (No authentication/No privacy)
- The authentication is performed by the specification and evaluation of the user name only. Data communication is not encrypted.
- AuthNoPriv (Authentication/No privacy)
- Authentication makes use of the hash algorithms set for the user. Data communication is not encrypted.
- AuthPriv (Authentication and privacy)
- Authentication makes use of the hash algorithms set for the user. Data communication is encrypted by DES or AES algorithms.
- Read
- Set the view of the MIB entries for which this group is to receive read rights. Available values are those defined under Views. Previously defined views are "Full Access". "LANmonitor Access". "Setup Access" and "Status Access".
- Write
- Set the view of the MIB entries for which this group is to receive write rights. Available values are those defined under Views. Previously defined views are "Full Access". "LANmonitor Access". "Setup Access" and "Status Access".
- Read-only traps
- Set the view of the MIB entries for which this group is to receive read rights for traps. Available values are those defined under Views. Previously defined views are "Full Access". "LANmonitor Access". "Setup Access" and "Status Access".
Views
Here you collect the different values or even entire branches of the device MIB, which each user is entitled to view or change in keeping with the corresponding access rights.
- Entry active
- Activates or deactivates this view.
- Name
- Enter a descriptive name for this view.
- OID subtree
- Use a comma-separated list of the relevant OIDs to decide which values and actions from the MIB are included in or excluded from this view.
Note: The OIDs can be found in the device MIB, which you can download from www.lancom-systems.com/downloads/.
- Access to subtree
- Here you decide whether the specified OID subtrees are "added" or "removed" from the view.
