The internal portal supports single sign-on to selected identity providers (IdP) using SAML. Microsoft Azure and Keycloak are supported.
Navigate to to open an editing window in which you can customize the settings for SAML.
You can configure the following elements in the SAML editing window:
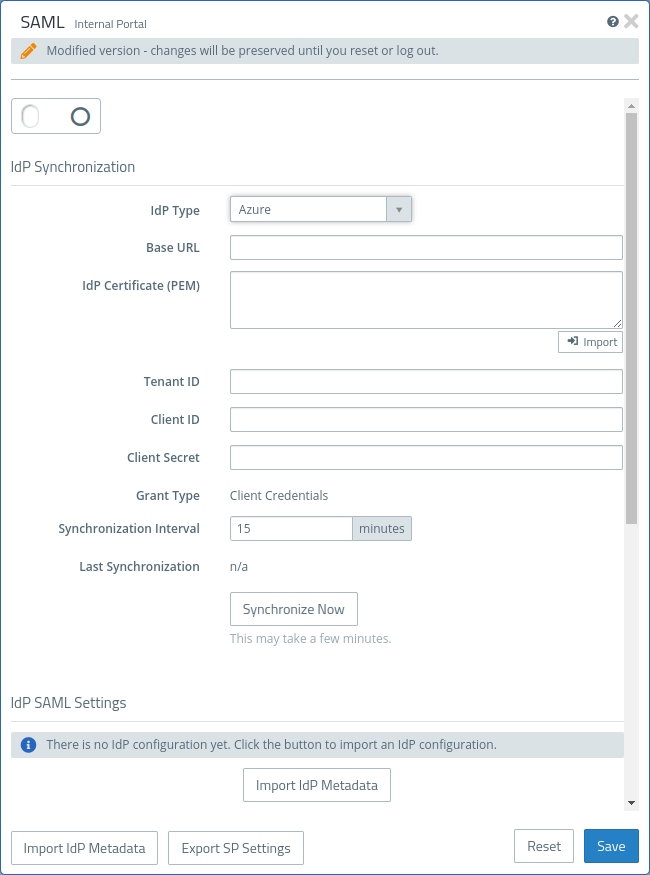
IdP Synchronization
These settings are necessary for connecting the firewall to the IdP. Lists of users and groups known to the IdP can then be queried via this connection.
| Input field | Description |
|---|---|
| I/0 | A slide switch indicates whether the SAML connection is currently active (I) or inactive (0). You can change the status by clicking on the slide switch. The SAML connection is deactivated by default. |
| IdP Type | Azure or Keycloak. The details vary depending on the type. |
| Base URL | The URL under which the IdP API can be reached. For Keycloak, this is the host name or IP address and the port of the Keycloak server. With Azure, the URL is made up of the host name (e.g. "https://sts.windows.net/") and the tenant ID. E.g. "https://sts.windows.net/ac564d8f-3367-c9a1-31dd-68e35de484ac" |
| IdP Certificate (PEM) | Optional. If the firewall connection to the IdP uses a certificate that the firewall does not trust, this can be stored here so that a secure connection can be established. This is helpful for self-signed certificates, for example. It can be entered in text form or imported from a file. |
| IdP Type Azure | |
| Tenant ID | Azure tenant ID. |
| Client ID | ID of the client configured on the IdP under which the queries are carried out. |
| Client Secret | Azure client secret. |
| Grant Type | Always "Client Credentials". |
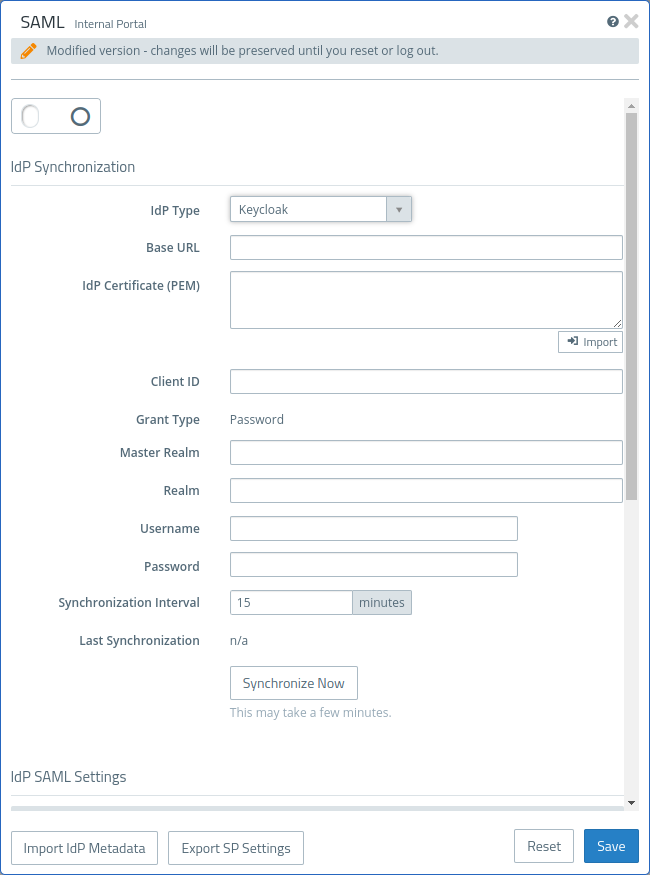
| IdP Type Keycloak | |
| Client ID | ID of the client configured on the IdP under which the queries are carried out. |
| Grant Type | Always "Password". |
| Master Realm | The Keycloak Master Realm. |
| Realm | The realm for which the users and groups are to be queried. |
| Username | User name for logging in to the Keycloak API. |
| Password | Password for logging in to the Keycloak API. |
| Synchronization Interval | Interval between the start of two synchronization processes. A synchronization process is only started if the previous synchronization process has been completed. If it is still running, nothing is done. After the interval has elapsed again, this check is repeated and a new synchronization process is started if necessary. |
| Last Synchronization | Time of the last synchronization process. A synchronization process can be started manually in the background via Synchronize Now. |
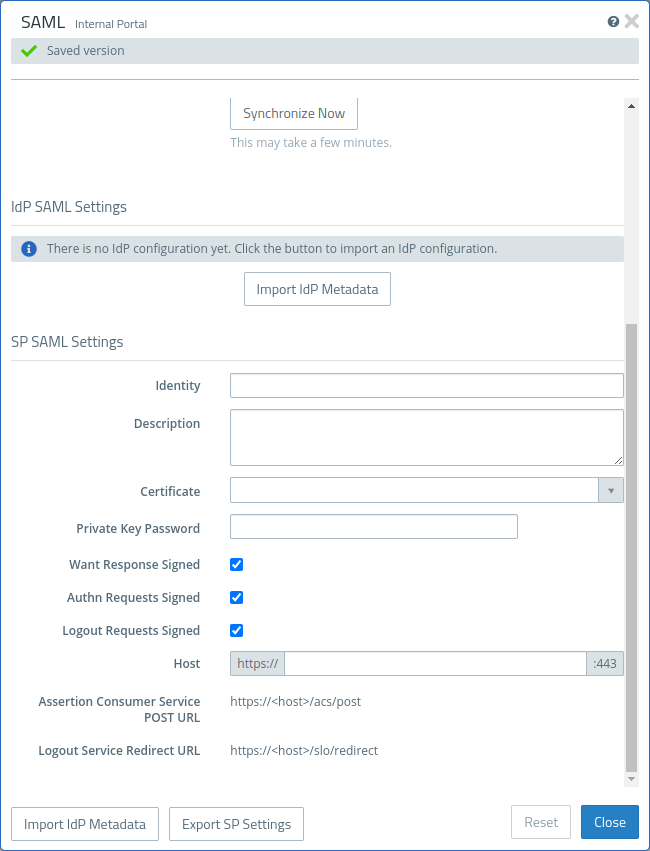
IdP SAML Settings
The IdP SAML settings are imported from the so-called "Federation Metadata" XML file. This file can be exported from the IdP. Its content depends on the respective settings in the IdP. If no metadata has been imported yet, the form displays the Import IdP Metadata button provided for this purpose. After the import, the transferred settings are displayed here. Changed IdP metadata can also be imported later using the Import IdP Metadata button at the bottom of the editor window.
SP SAML Settings
The SP-SAML settings describe where and how the service provider running on the firewall can be reached for SAML authentication. The service provider settings can be exported as an XML file. This XML file can then be imported into the IdP to apply the relevant settings.
| Input field | Description |
|---|---|
| Identity | A freely selectable identifier for the service provider. E.g. the firewall name. |
| Description | An optional description. |
| Certificate | The certificate. Note: Azure only supports certificates with a key size of 2048
bits due to a limitation of Azure.
|
| Private Key Password | The password for the private key of the certificate used. |
| Want Response Signed | If this option is activated, responses from the firewall are signed. |
| Authn Requests Signed | If this option is activated, only correctly signed Authn requests are accepted. |
| Logout Requests Signed | If this option is activated, only correctly signed logout requests are accepted. |
| Host | Host address at which the client can reach the service provider.The port always corresponds to the Web Login Port of the internal portal (). The host part can be freely selected. An IP address or an appropriately resolving host name that belongs to an intranet interface of the firewall should be specified here. The internal portal and the service provider can only be accessed on these interfaces. |
| Assertion Consumer Service POST URL | URL to which the client browser is redirected as part of the login process. Results from the host address. |
| Logout Service Redircect URL | URL to which the client browser is redirected as part of the logout process. Results from the host address. |
Users of the IdP for the internal portal
- the administration of content filter override codes (),
- the set of rules on the desktop (user and group objects, both simple and VPN variants) and
- the Wake on LAN function ().
