Simple masquerading has the effect, that all IP addresses in the local network are masked behind the IP address of the router. But when using simple masquerading if a certain computer on the LAN is supposed to be available for stations on the internet (e.g. FTP server) the IP address of the FTP server is not visible either. A connection to this FTP server from the internet in not possible.
To enable the access to such a server (’exposed host’) in the LAN, the IP address of the FTP server must be entered with all services that are also supposed to be available from outside the LAN. If a computer sends a packet from the Internet to, for example, an FTP server on the LAN , from the point of view of this computer the router appears to be the FTP server. The router reads the IP address of the FTP server in the LAN from the entry in the service table. The packet is forwarded to this computer. All packets that come from the FTP server in the LAN (answers from the server) are hidden behind the IP address of the router.
The only small difference is that:
- Access to a service (port) in the intranet from outside must be defined in advance by specifying a port number. The destination port is specified with the intranet address of, for example, the FTP server, in a service table to achieve this.
- When accessing the Internet from the LAN, on the other hand, the
router itself makes the entry in the port and IP address information
table. Note: The table concerned can hold up to 2048 entries, that is it allows 2048 simultaneous transmissions between the masked and the unmasked network.After a specified period of time, the router, however, assumes that the entry is no longer required and deletes it automatically from the table.Note: Stateful Inspection and inverse masquerading: If in the Masquerading module a port is exposed (i.e. all packets received on this port should be forwarded to a server in the local area network), then this requires with a Deny All Firewall strategy an additional entry in the Stateful Inspection Firewall, which enables the access of all stations to the respective server.
On occasion it is desirable for the "exposed" host not to be contacted over this standard port, e.g. when security reasons demand the use of another port.
In this case not only the implementation of ports to an IP address is necessary, but as well the implementation to other ports (port mapping). Another example of use for this port implementation is the implementation of several ports of the WAN to a shared port in the LAN, which can be assigned to different IP addresses (N-IP-Mapping).
The configuration of port mapping involves the assignment of a port or port range (start port to end port) to an IP address from the LAN as the target and the port (map port) to be used in the LAN.
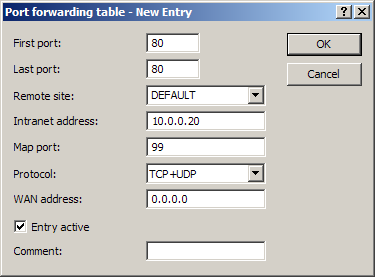
LANconfig: IP-Router / Masquerading / Port-Forwarding table
WEBconfig: LCOS-menu tree / Setup / IP-Router / 1-N-NAT / Service table
- Start port D-port from (start port)
- End port D-port to (end port)
- Remote site
Remote site which applies for this entry.
- The use of virtual routers requires for the port forwarding a specific selection of the remote station. If no peer is entered then the entry applies to all peers.
- Intranet-Adresse Internet address that a packet within the port range is forwarded to.
- Map port
Port used for forwarding the packet.
Note: If "0" is entered for the map port, the ports used in the LAN will be the same as those used in the WAN. If a port range is to be mapped, then the map port identifies the first LAN port to be used. For example, mapping the port range '1200' to '1205' to the internal map port '1000' means that the ports 1000 to 1005 will be used for data transfer in the LAN.Note: Port mapping is static, meaning that two ports or port ranges cannot be mapped to the same map port of a target computer in the LAN. The same port mapping can be used for different target computers.
- Protocol Protocol which applies for this entry.
- WAN address WAN address which applies for this entry. If the device has more than one static IP address, then this allows port forwarding to be limited to certain connections.
- Entry active Switches the entry on or off.
- Comment Comment on the defined entry (64 characters)