In this table, you configure the parameters for IKEv2 authentication of the local and at least one remote identifier.
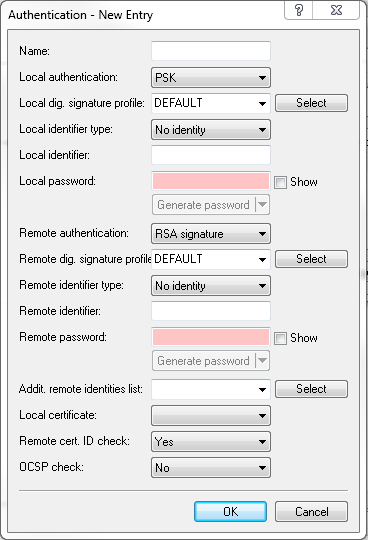
- Name
- Contains the unique name of this entry. You assign this name to the connections in the Connection list in the "Authentication" field.
- Local authentication
- Sets the authentication method for the local identity. Possible values are:
- PSK: Pre-shared key:
- RSA-Signature: Use of digital certificates with private RSA key and RSA signature scheme
- Digital signature: Use of configurable authentication methods with digital certificates as per RFC 7427. This procedure is an extensible and flexible authentication technique that allows padding and hash algorithms to be configured freely.
- Local digital signature profile
- The profile name of the local digital signature profile that is used.
- Local identifier type
- Displays the ID type of the local identity. The device interprets the entry under "Local identifier" accordingly. Possible entries are:
- No identity: No identity is transmitted.
- IPv4 address: The device uses an IPv4 address as a local ID.
- IPv6 address: The device uses an IPv6 address as a local ID.
- Domain name (FQDN): The device uses a domain name as a local ID.
- E-mail address (FQUN): The device uses an e-mail address as a local ID.
- ASN.1 Distinguished Name: The device uses a distinguished name as a local ID (e.g. "CN=client01.example.com,O=test,C=DE").
- Key ID (group name): The device uses the group name as a local ID. You can set any group name.
- Local identifier
- Contains the local identity. The significance of this entry depends on the setting under "Local identifier type".
- Local password
- Contains the password of the local identity. The device uses this password to authenticate at the remote site. The local and remote password can be identical or different.
- Remote authentication
- Sets the authentication method for the remote identity. Possible values are:
- PSK: Pre-shared key:
- RSA-Signature: Use of digital certificates with private RSA key and RSA signature scheme
- Digital signature: Use of configurable authentication methods with digital certificates as per RFC 7427. This procedure is an extensible and flexible authentication technique that allows padding and hash algorithms to be configured freely.
- Remote digital signature profile
- The profile name of the remote digital signature profile.
- Remote identifier type
- Displays the ID type that the device expects from the remote identifier. The device interprets the entry under "Remote identifier" accordingly. Possible entries are:
- No identity: The device accepts any ID from the remote device. The device to ignores entries in the "Remote identifier" field.
- IPv4 address: The device expects an IPv4 address as the remote ID.
- IPv6 address: The device expects an IPv6 address as the remote ID.
- Domain name (FQDN): The device expects a domain name as the remote ID.
- E-mail address (FQUN): The device expects an e-mail address as the remote ID.
- ASN.1 Distinguished Name: The device expects a distinguished name as a remote ID (e.g. "CN=client01.example.com,O=test,C=DE").
- Key ID (group name): The device expects the group name as the remote ID.
- Remote identifier
- Contains the remote identity. The significance of this entry depends on the setting under "Remote identifier type".
- Remote password
- Contains the password of the remote identity.
- Addit. remote identities list
- Redundant VPN scenarios allow the use of alternative remote identities. Here you configure additional remote identities from the table .
- Local certificate
- Displays the local certificate.
- Remote certificate check
- This option determines whether the device checks that the specified remote identity is included in the received certificate.