To configure key settings, go to .
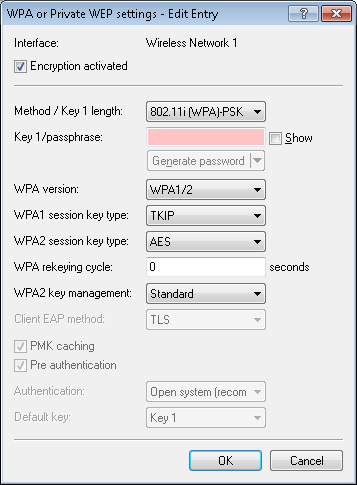
- Enable encryption
- Enable or disable encryption for this WLAN interface.
- Method/key 1 length
- Set the encryption method to be used here. Possible values are:
- 802.11i (WPA)-PSK – Encryption according to the 802.11i standard offers the highest security. The 128-bit AES encryption used here offers security equivalent to that of a VPN connection. Select this setting if no RADIUS server is available and authentication is based on a pre-shared key.
- 802.11i (WPA)-802.1x – If authentication is handled by a RADIUS server, select the option '802.11i (WPA)-802.1x'. When using this setting, additionally ensure that the RADIUS server is configured in the 802.1x settings.
- WEP 152, WEP 128, WEP 64 – encryption according to the WEP standard with key lengths of 128, 104 or 40 bits respectively. This setting is only to be recommended when the hardware used by the WLAN client does not support the modern method.
- WEP 152-802.1x, WEP 128-802.1x, WEP 64-802.1x – encryption according to the WEP standard with key lengths of 128, 104 or 40 bits respectively, and with additional authentication via 802.1x/EAP. This setting is also only to be recommended when the hardware used by the WLAN client does not support the 802.11i standard. The 802.1x/EAP authentication offers a higher level of security than WEP encryption alone.
- Key 1/passphrase
- In line with the encryption method activated, you can enter a special WEP key for the respective logical WLAN interface or a passphrase when using WPA-PSK:
- The passphrase, or the 'password' for the WPA-PSK method, is entered as a string of at least 8 and up to 63 ASCII characters.Anmerkung: Please be aware that the security of this encryption method depends on the confidential treatment of this passphrase. Passphrases should not be made public to larger circles of users.
- The WEP key 1, that applies only to its respective logical WLAN interface, can be entered in different ways depending on the key length. Rules for entering the keys can be found in the description of the WEP group key.
- The passphrase, or the 'password' for the WPA-PSK method, is entered as a string of at least 8 and up to 63 ASCII characters.
- WPA version
- WPA version for encryption offered by the access point to the WLAN clients.
- WPA1: WPA2 only
- WPA2: WPA2 only
- WPA1/2: WPA1 and WPA2 in one SSID (radio cell)
- WPA 1 session key type
- If '802.11i (WPA)-PSK' has been entered as the encryption method, the procedure for generating a session or group key for WPA 1 can be selected here:
- AES – the AES method will be used.
- TKIP – the TKIP method will be used.
- AES/TKIP – the AES method will be used. If the client hardware does not support the AES method, TKIP will be used.
- WPA 2 session key type
- Procedure for generating a session or group key for WPA 2.
- WPA2 key management
- Here you specify which standard the WPA2 key management should follow. Possible values are:
- Standard: Enables key management according to the IEEE 802.11i standard without Fast Roaming and with keys based on SHA-1. Depending on the configuration, the WLAN clients in this case must use opportunistic key caching, PMK caching or pre-authentication.
- SHA256: Enables key management according to the IEEE 802.11w standard with keys based on SHA-256.
- Fast roaming: Enables fast roaming as per 802.11r
- Combinations of the three settings
Wichtig: Although it is possible to make multiple selections, this is advisable only if you are sure that the clients attempting to login to the access point are compatible. Unsuitable clients may refuse a connection if an option other than Standard is enabled. - WPA rekeying cycle
- A 48-bit long initialization vector (IV) impedes attackers in their attempts to calculate the WPA key. The true key consisting of the IV and WPA key only repeats every 16 million packets. In high-traffic WLANs, the key is repeated only after several hours. To avoid repetition of the key, WPA automatically renegotiates the key at regular intervals. This takes place before repetition of the key. Enter a value in seconds after which the key is renegotiated. The standard value is '0' and the key is not negotiated in advance.
- Client EAP method
- LANCOM access points in WLAN client operating mode can authenticate themselves to another access point using EAP/802.1X. To activate the EAP/802.1X authentication in client mode, the client EAP method is selected as the encryption method for the first logical WLAN network.
Please note that the selected client EAP method must match the settings of the access point that this LANCOM access point is attempting to register with.
Anmerkung: In addition to setting the client EAP method, also be sure to observe the corresponding setting for the WLAN client operation mode. The client EAP method setting has no function on logical WLAN networks other than WLAN 1.
- Authentication
- If the encryption method was set as WEP encryption, two different methods for the authentication of the WLAN client are available:
- The 'Open system' method does not use any authentication. The data packets must be properly encrypted from the start to be accepted by the access point.
- With the 'Shared key' method, the first data packet is transmitted unencrypted and must be sent back by the client correctly encrypted. This method presents potential attackers with at least one data packet that is unencrypted.
- Default key
- If WEP encryption is selected, the access point can select from four different WEP keys for each logical WLAN interface:
- Three WEP keys for the physical interface
- An additional WEP key particular to each logical WLAN interface